How to use AD Authentication to access Reports and DMCS
How to add Azure AD authentication for end-user notification reports
To make sure that end-users are using the AD login to access the notification report you must:
1. Enforce authentication for subscribers to a notification policy
2. Register at Azure App for AD synchronization
Please make sure that the domain that the notification report is on is publicly available. Eg. if the notifications report is on: https://gdpr.myorganisations.com then the domain gdpr.myorganisations.com must be publicly available.
IT does NOT have to be publicly accessible. It can be IP restricted but must be publicly resolved.
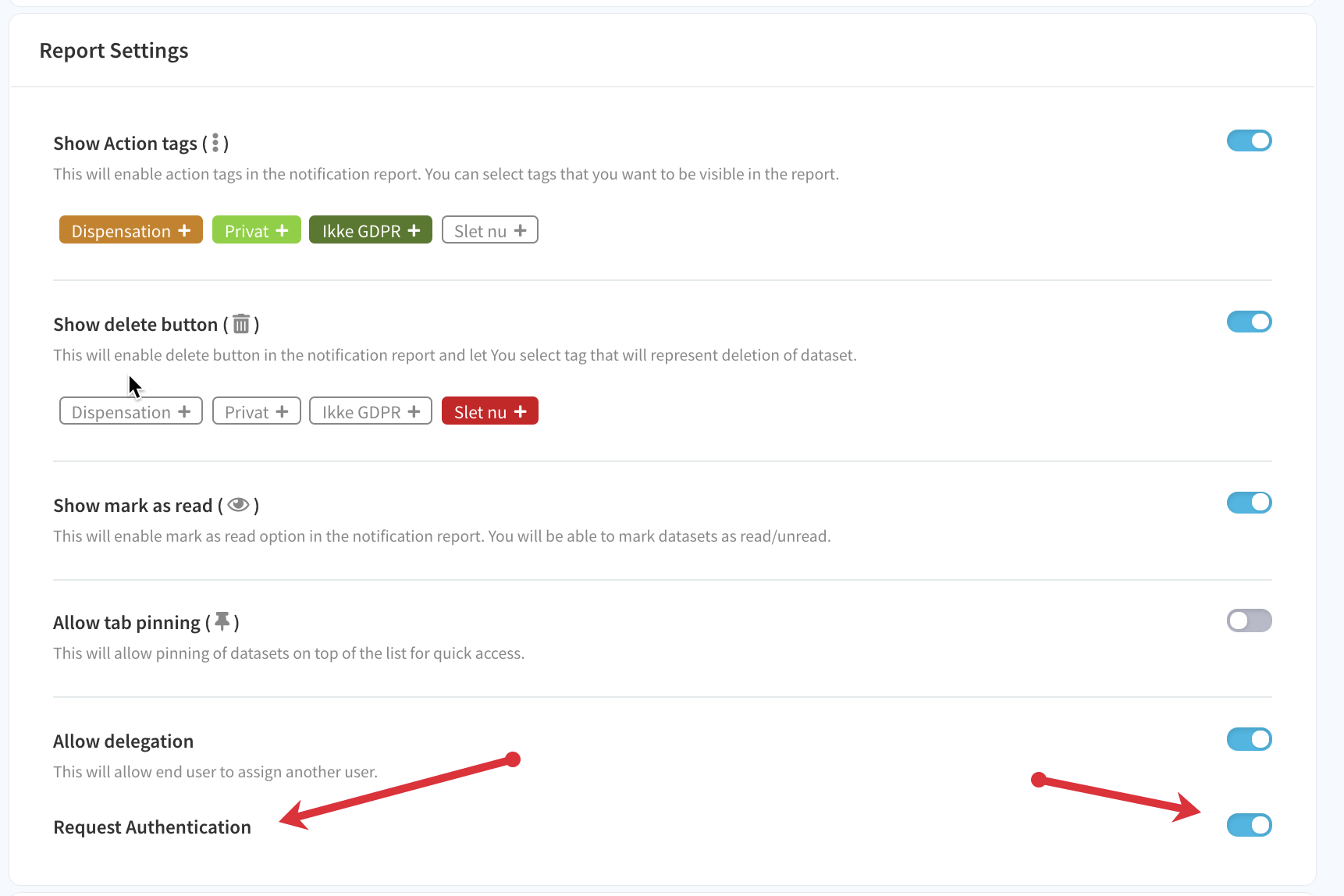
Enforce authentication for subscribers to a notification policy
Go to the notification report -> Edit Report -> Edit Settings -> Request Authentication
Register at Azure App for AD synchronization
1 Go to portal.azure.com --> App registration and click new Registration 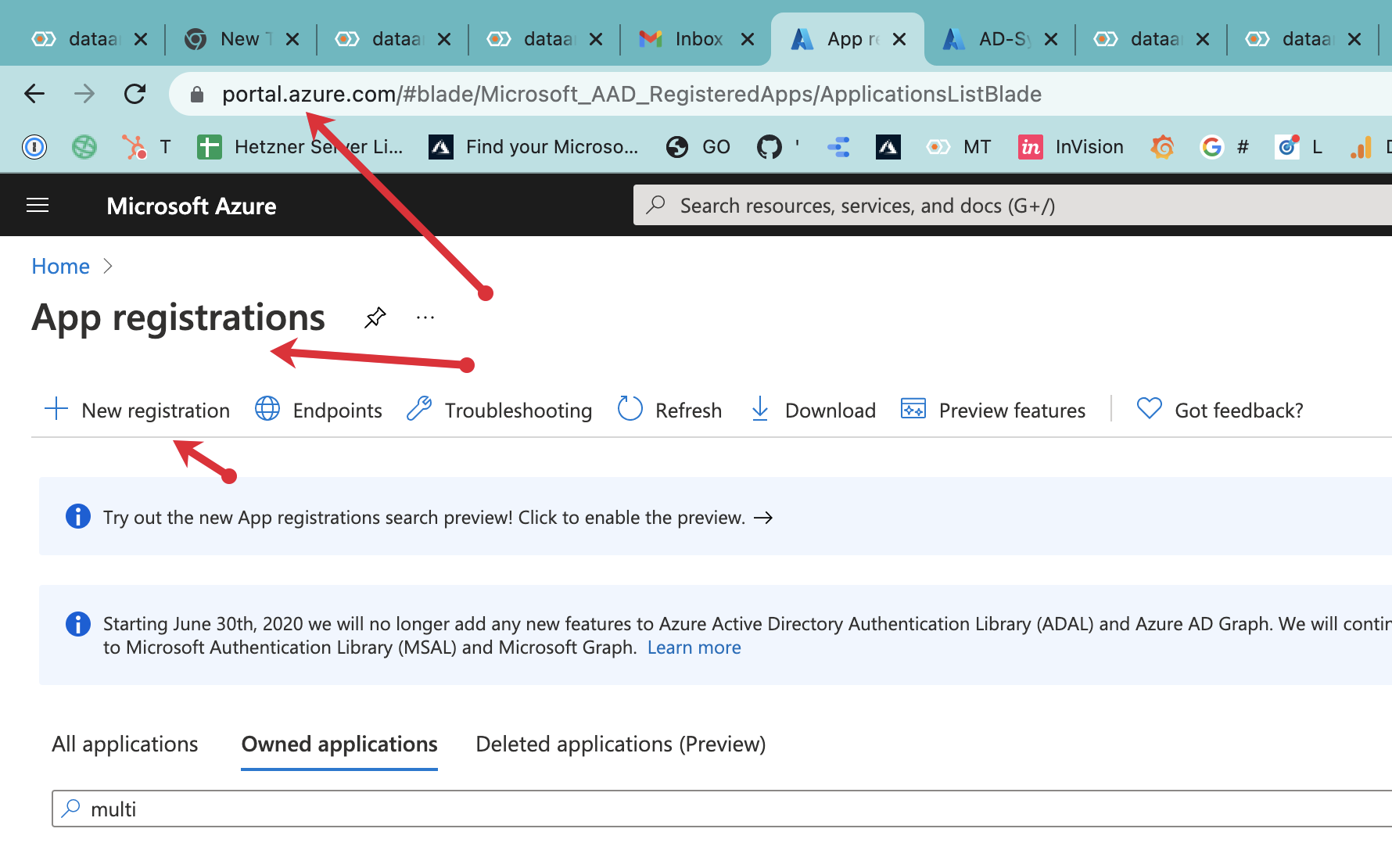
2. Give the App registration the name DAM_AD_Sync
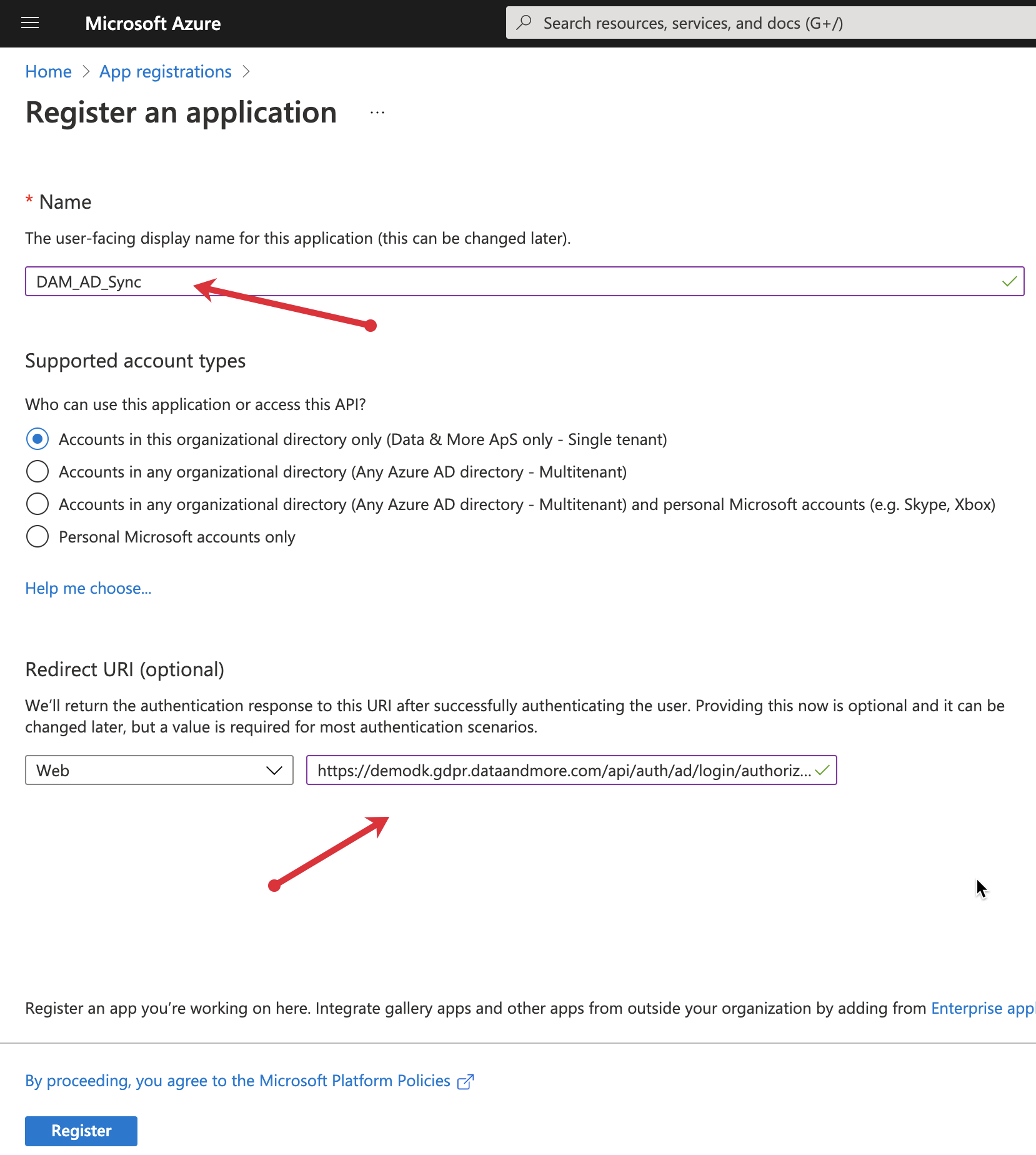
3. Add the proper redirect URL in the form
"the gdpr server domain" + "/api/auth/ad/login/authorized"
So if your gdpr server domain is: https://demodk.gdpr.dataandmore.com the redirect URL should be:
https://demodk.gdpr.dataandmore.com/api/auth/ad/login/authorized
4. Click Register
5. Copy and store the Application (client) ID and store it in a safe location
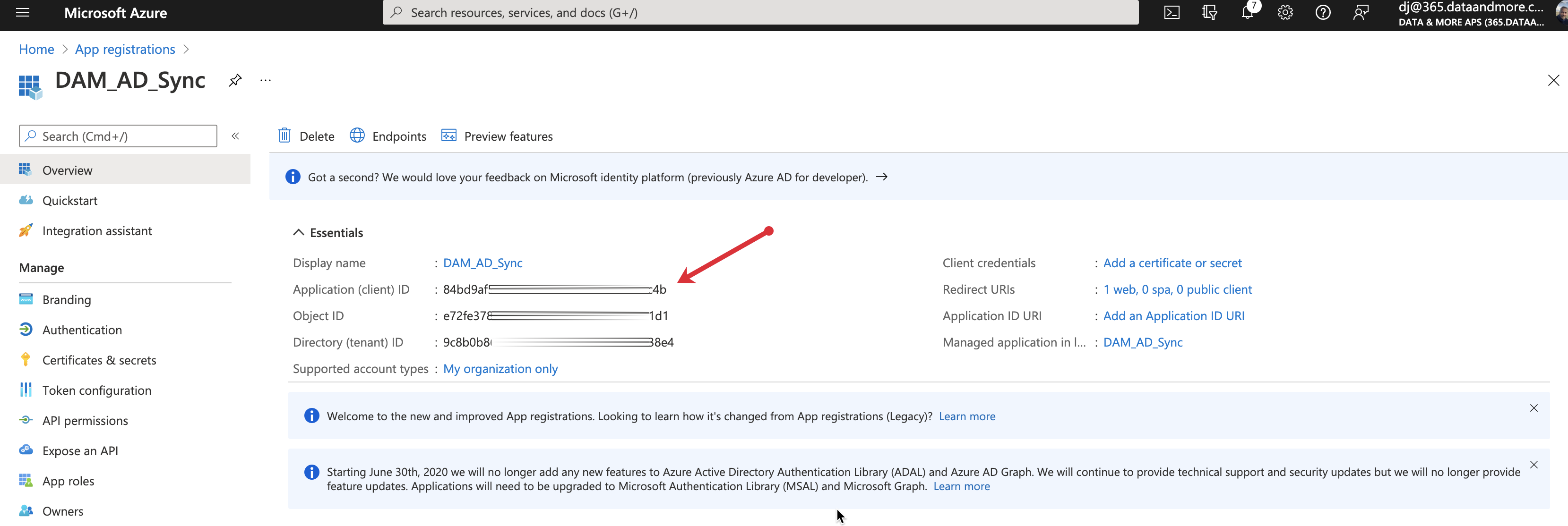
6. go to API permissions and click
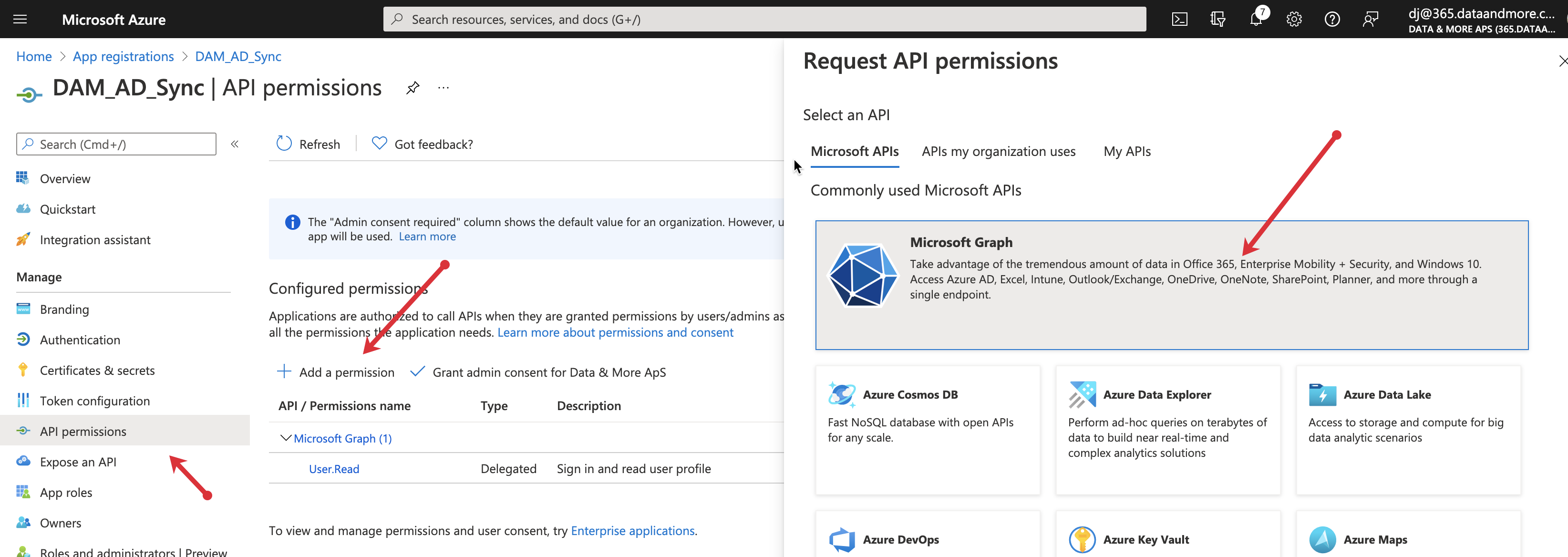
- API permission
- Add a permission
- Microsoft Graph
- Application Permissions
Search for User and select
- User.Export.All
- User.Read.All
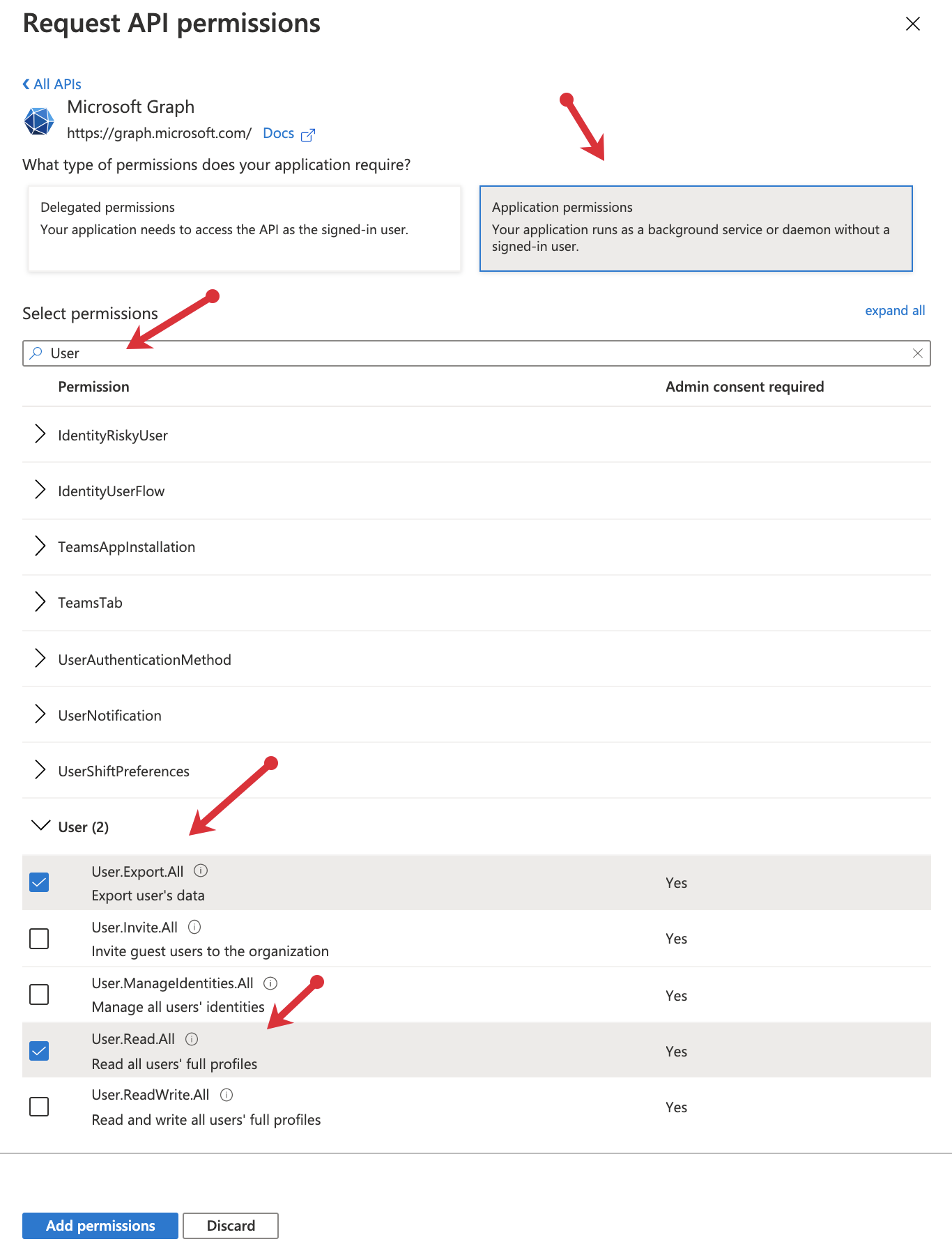
7. Click "Add permission" and "Grant admin consent for (your tenant)"
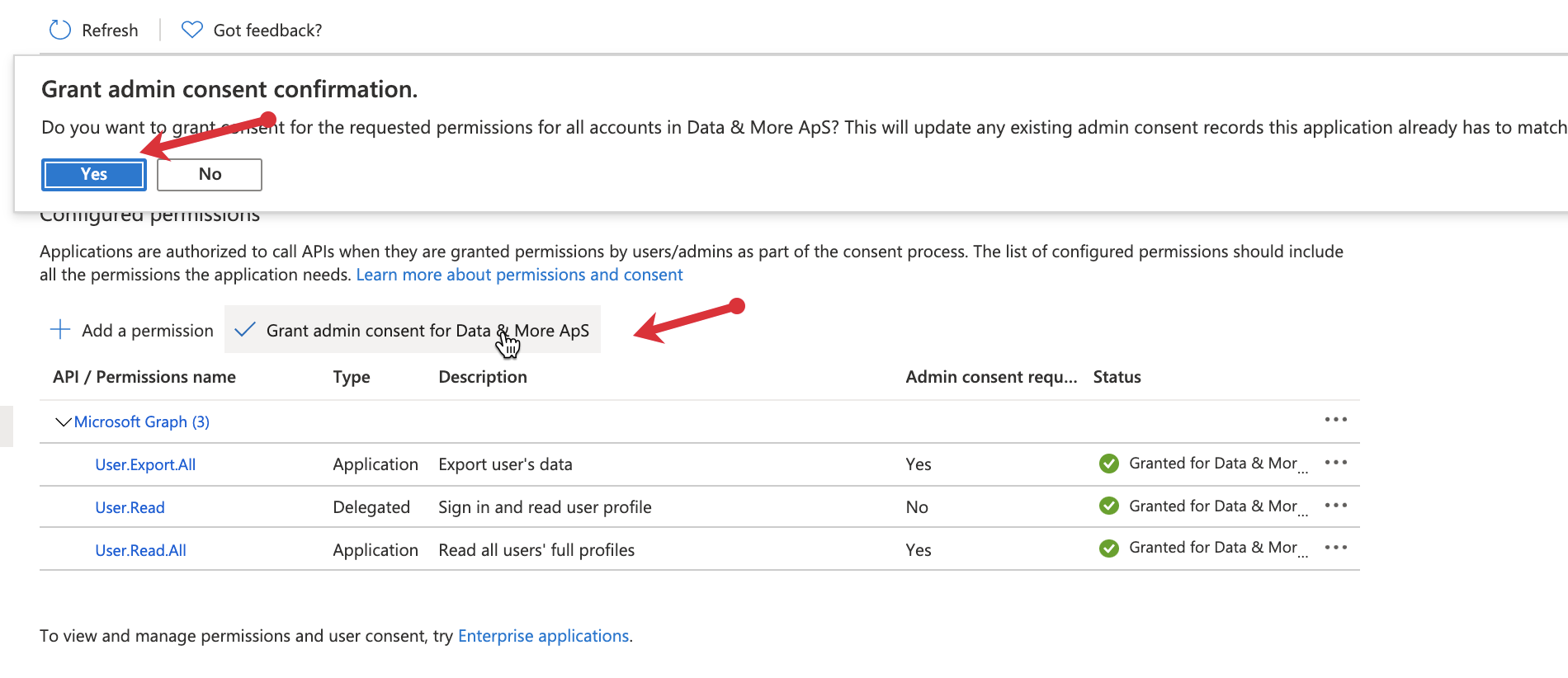
8. Go to “Certificates & Secrets.
9. Add a “New client secrets” → provide a “Description” → Select experts “Never” → “Add.”
20. Store the client secret VALUE securely. IT CANNOT BE RETRIEVED
21. Go to settings in the Data & More Toolbox and enter the client ID + Secret Value + tenant
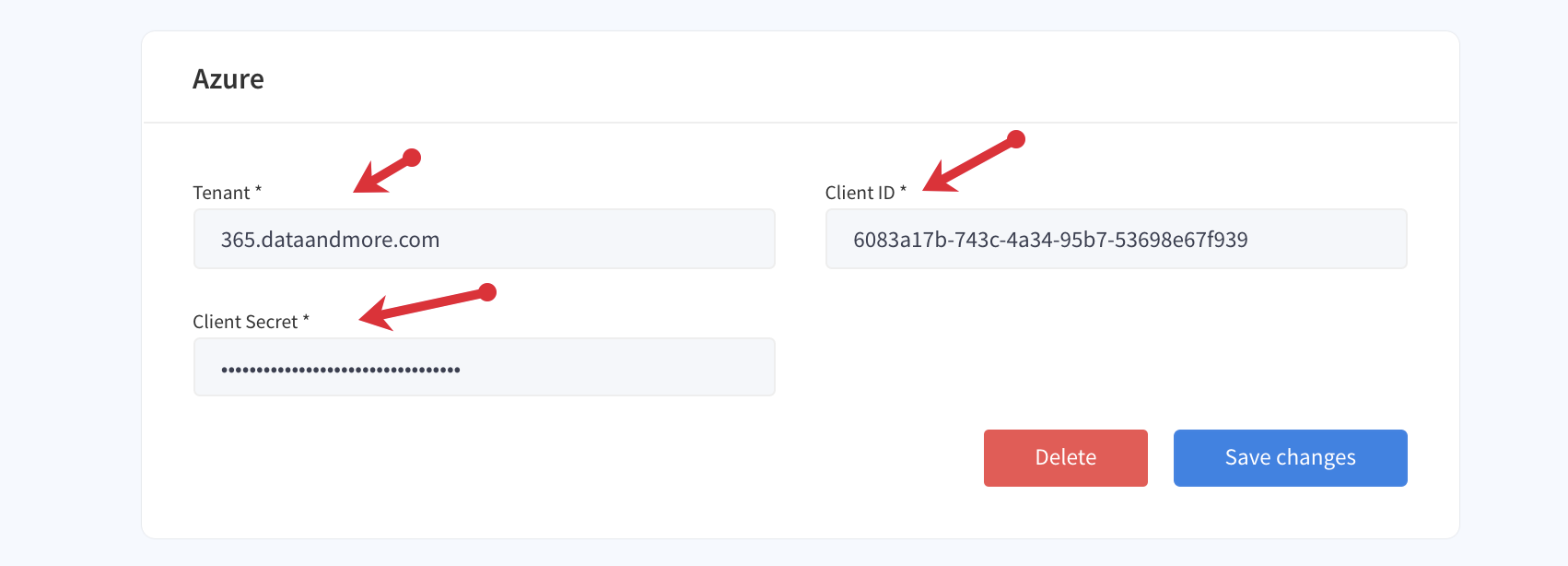
If you don't have access to the Data & More server please send the client ID (from number five) to support@dataandmore.com and send the secret value (from number 20) to your contact D&M person's personal email.
